New chip architecture opens up the era of security operation
At this year's Hot Chips conference, industry experts called for a new generation of security-designed computer architecture to avoid the recurrence of Spectre/Meltdown security breaches at the beginning of the year...
At this year's Hot Chips 2018 conference, industry experts called for a new generation of security-designed computers. Microsoft and Google, respectively, describing hardware architectures that structurally are different but similar, have taken an important step in this direction.
After uncovering the Spectre/Meltdown security vulnerability earlier this year, engineers were awakened to possibility that decades-old techniques like speculative execution could open the door to bypass attacks. Just a Red Hat has to spend tens of thousands of engineering hours to fix flaws in Linux. Moreover, chip manufacturers such as AMD, ARM, IBM and Intel must do a small amount of work. Therefore, it is estimated that the industry will lose millions of dollars.
Experts say that current patches solve the problem but they failure to fix potential vulnerabilities, leaving some of them likely to persist for years. Last week there were even new attack variants that are expected to continue in the foreseeable future.
Experts call for a new generation of computer architecture
"There are many bypass channels that can’t be closed... This is a series of things to be changed and it will take a long time," said John Hennessy, a senior processor architect and chairman of Google’s parent company Alphabet. Thus, in his keynote address Mr Hennessy called on the industry to launch a new era of security.
Jon Masters, who oversees security at Red Hat, said Red Hat has created an initial set of Spectre/Meltdown patched for eight wafer architectures to support 15 Linux versions, spending a total of 10,000 hours of engineering effort. The new variant discovered last week, cost more than 10,000 hours partly due to its core and VM management programs.
Mark Hill, a professor of computer science at the University of Wisconsin at Madison, said in a panel discussion: "We need computer architecture 2.0 to define operations without loopholes - but the problem is we don't know what to do."
Hill listed a long list of techniques for protecting processors, such as isolating branch predictors, partition caches and reducing aliasing. "There are various possibilities, but none of them is good." He also pointed out that it is still unclear whether the security issues can be fully repaired or only partially resolved.
Ruby Lee, a senior security researcher at Princeton University, said: "I am glad to hear experts like John Hennessy calling for a security era. It's better to be late than never."
She added: "The benefit is not just to fix one problem at a time, although this is what the security industry wants to do. The first principle of the security architecture should be unauthorized access.”
Several speakers also called for more work on opening source software and hardware. Masters said: "We have seen many attacks against closed microcode in machines. Unauthenticated behavior is incredible as long as it’s invisible."
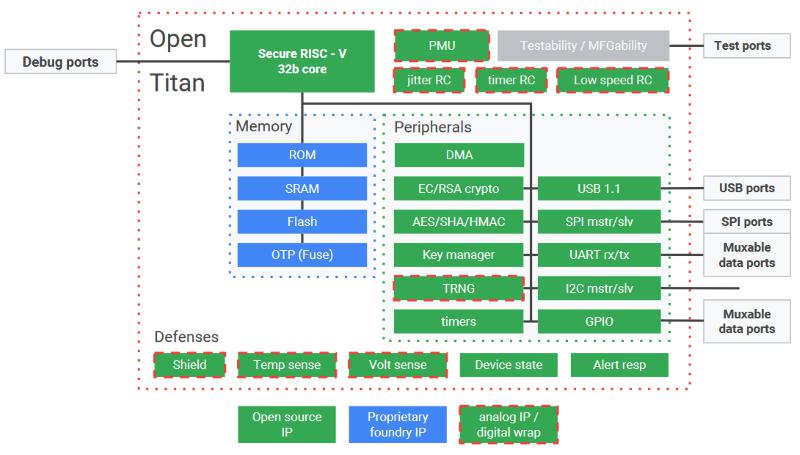
Google is aiming to release a plan next year to promote an open source version of its Titan security module—possibly with a 32-bit RISC-V core (source: Google)
Google and Microsoft are neck and neck.
Microsoft described the Pluton security module for its Azure IoT service at this year's event, while Google gave another detailed introduction to Titan, a similar module for marking and protecting systems in its data center. Despite their different goals, both approaches adopted very similar principles and functions, allowing a Google engineer on the scene to suggest that the two companies could merge into a standard one day.
Pluton and Titan enforce encrypted authentication for security system startup and device identification. Both chips contain a random number generator and all the hardware modules responsible for generating keys, which the software cannot accessed. In addition, both chips use e-fuse settings to control module state to prevent tampering during manufacturing and lifecycle.
One of the biggest differences between the two approaches is how to enter the market in the future. Microsoft will work with Mediatek to build Pluton for the first time in a Wi-Fi router chip. The company is targeted at cooperating with many other MCU and SoC vendors.
So far, Google has developed two Titan schemes, one of which was the announcement last year to protect its data centre. Another unknown version is currently used by Google employees as a second factor in USB dongle authentication.
Now Google is setting up an industry organization for this, and is expected to launch Titan's open source solution next year, possibly with a 32-bit RISC-V core. This open source version will be available for any embedded or consumer product.
Google engineers hope that the so-called Open Titan program will attract other businesses like Microsoft. Through the joint efforts of industry partners, it will help to gradually shape established standards to create a security architecture similar to that described by Hill and others. However, this concept is yet insignificant for some Google engineers.
In the short term, Microsoft wishes that Pluton will become a selling point for its Azure IoT cloud service. It is expected that various companies, including other cloud services and MCU vendors, will release their own security architectures and solutions.
The good news is that after Spectre/Meltdown security loophole, engineers will actively create safer products. In contrast, the bad is that they are worried about more serious hacking attacks before customers are willing to pay.
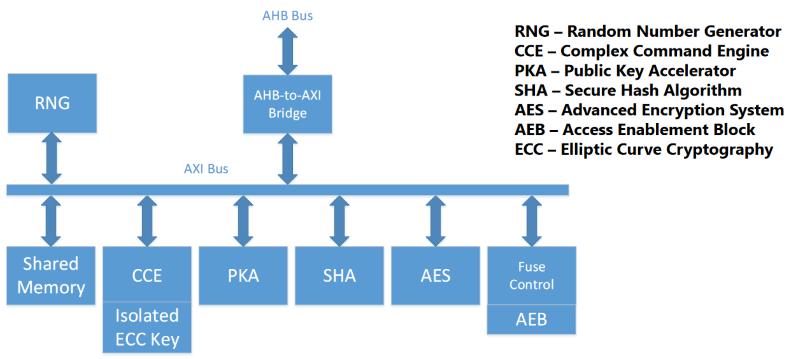
Microsoft's Pluton generally supports features and modules similar to Google’s Titan, but Pluton is still part of Microsoft's IoT secret weapon (Source: Microsoft)
